There is a new vulnerability for Blackberrys worldwide. Thought we were so safe didn't we? Recently discovered was the ability for hackers to execute phishing attacks on your Blackberry. This bug relates to the Browser dialog box that provides
information about web site domain names and their associated
certificates. The BlackBerry Browser dialog box informs the BlackBerry
device user when there is a mismatch between the site domain name and
the domain name indicated in the associated certificate, but does not
properly illustrate that the mismatch is due to the presence of some
hidden characters (for example, null characters) in the site domain
name.
A
malicious user could create a web site that includes a certificate that
is purposely altered using null (hidden) characters in the certificate's Common Name (CN) field or otherwise manipulated to deceive a BlackBerry device user into believing they have connected to a trusted web site.
If the
malicious user then performs a phishing-style attack by sending the
BlackBerry device user a link to the web site in an SMS or email
message that appears to be from a trusted source, and the BlackBerry
device user chooses to access that site, the BlackBerry Browser will
correctly detect the mismatch between the certificate and the domain
name and display a dialog box that prompts the user to close the
connection. However, the dialog box does not
display null characters, so the user may believe they are connecting to
a trusted site and disregard the recommended action to close the
connection.
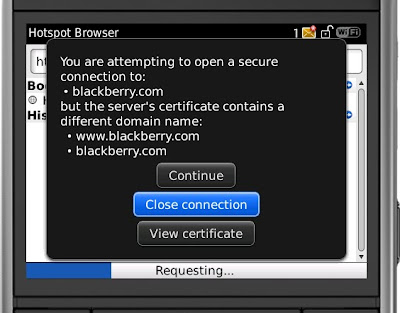
BlackBerry
Browser dialog box that does not clearly indicate that there is a
mismatch between the web server address and its associated certificate:
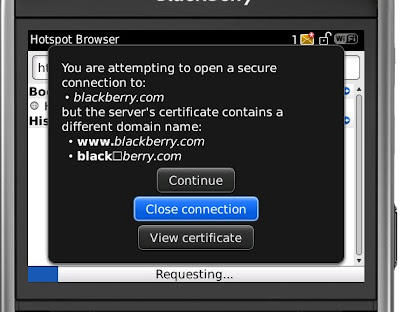
BlackBerry Browser dialog box that represents a previously hidden null
character with a block and highlights (in bold) the non-matching
portion of the domain name:
Check with your smartphone carrier to see if they have received the OS update.
 RSS Feed
RSS Feed Twitter
Twitter